Non-Proprietary Security Policy, Version 0.7
January 4, 2008
Software House iSTAR eX Controller
Page 24 of 27
© 2008 Software House
2. On the "System Variable => Key Management Policy" screen of the Admin program, select the Custom
st and to the
g the new certificates.
5. For each cluster, change its encryption mode to FIPS.
luster in the CCURE 800/8000
r you. There is a column in the generated report which will indicate in
1. Generate CA, host, and controller certificate.
Host Certificates option.
3. The system will automatically copy and download the new custom certificates to the ho
controllers.
4. All communicating iSTAR eX controllers will reboot and come back usin
6. The system automatically tells the controllers to run in FIPS mode.
7. Stunnel service running on the CCURE host restarts.
8. All communicating controllers reboot and come back in FIPS mode
3.2.3
Verifying FIPS Mode of Operation
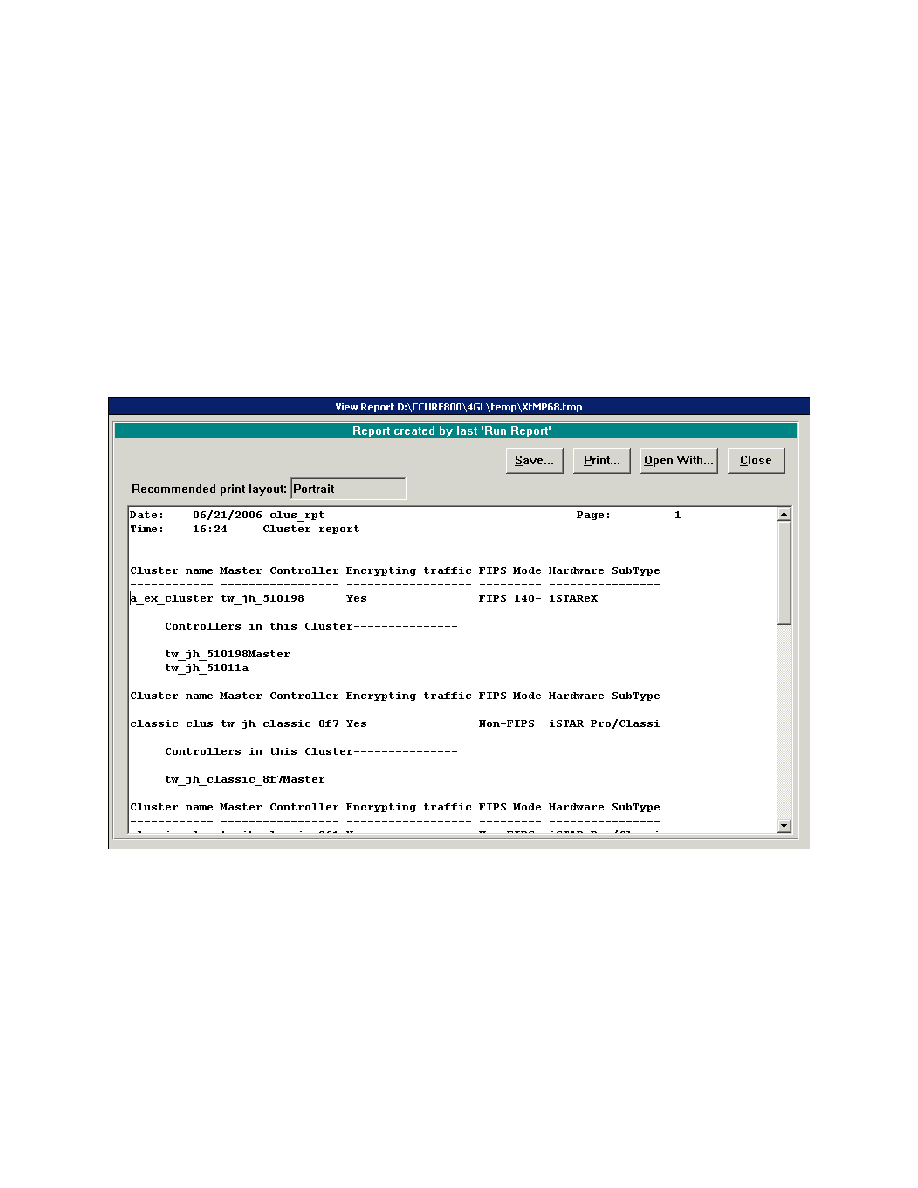
To see if you are operating in FIPS mode, go to Report => Hardware => iSTAR C
host server, and it will generate a report fo
what mode the cluster is running. It will either say "non-FIPS" or "FIPS 140-" (see in Figure 9 below).
idance
Figure 9 FIPS Mode Report
3.3 Crypto Officer Gu
The Crypto Officer is the person responsible for setting up, configuring, and administrating the iSTAR eX.
This document may be freely reproduced and distributed whole and intact including this copyright notice.

