QTI Crypto Engine Core
FIPS 140-2 Non-Proprietary Security Policy
© 2016 Qualcomm Technologies, Inc.
This document can be reproduced and distributed only whole and intact, including this copyright notice.
6 of 23
1.
Caveat: AES counter mode uses a 128 bit counter. The counter will roll over after 2^128
blocks of encrypted data.
2.1.1.Hardware description
The cryptographic module is implemented in the QTI Crypto Engine Core 5.3.1 hardware, which
resides in Qualcomm Snapdragon 820 processors
(https://www.qualcomm.com/products/snapdragon/processors/820). The QTI Crypto Engine Core
5.3.1 provides a series of algorithms (as listed in Table 2-1) implemented in the device hardware.
2.1.2.Module Validation Level
The module is intended to meet requirements of FIPS 140-2 at an overall Security Level 2. The
following table shows the security level claimed for each of the eleven sections that comprise the
validation:
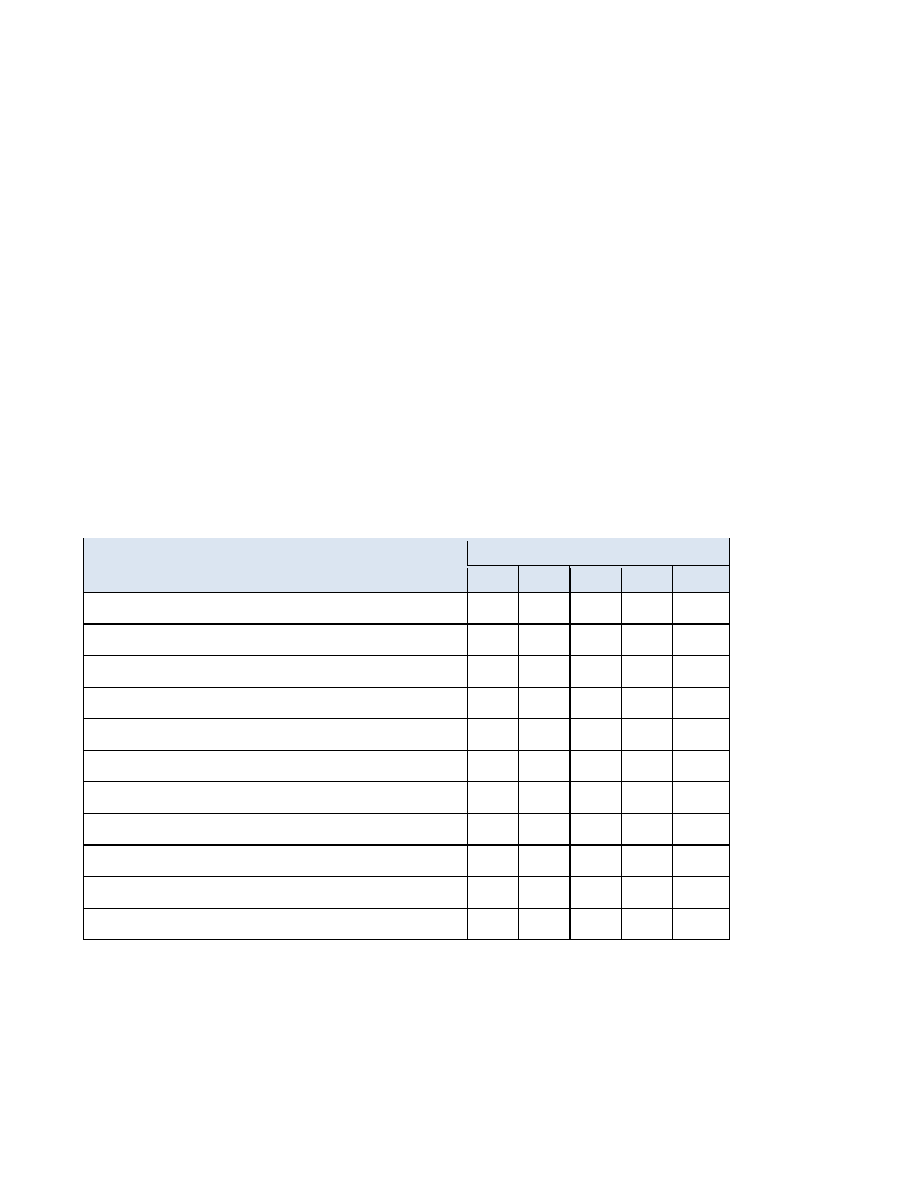
Table 2-2: Security Levels
FIPS 140-2 Sections
Security Level
N/A
1
2
3
4
Cryptographic Module Specification
X
Cryptographic Module Ports and Interfaces
X
Roles, Services and Authentication
X
Finite State Model
X
Physical Security
X
Operational Environment
X
Cryptographic Key Management
X
EMI/EMC
X
Self Tests
X
Design Assurance
X
Mitigation of Other Attacks
X
The QTI Crypto Engine Core is classified as a single-chip hardware module for the purpose of FIPS
140-2 validation. The logical cryptographic boundary for the module is the sub-chip implementing
the module while the physical boundary is the Qualcomm Snapdragon 820 SoC.
The module was tested as a sub-chip implemented within the Qualcomm Snapdragon 820 SoC.
2.2.Description of Modes of Operations

