Copyright Pure Storage Inc., 2015
Version 1.1
Page
11 of 17
Pure Storage Inc. Public Material May be reproduced only in its original entirety (without revision).
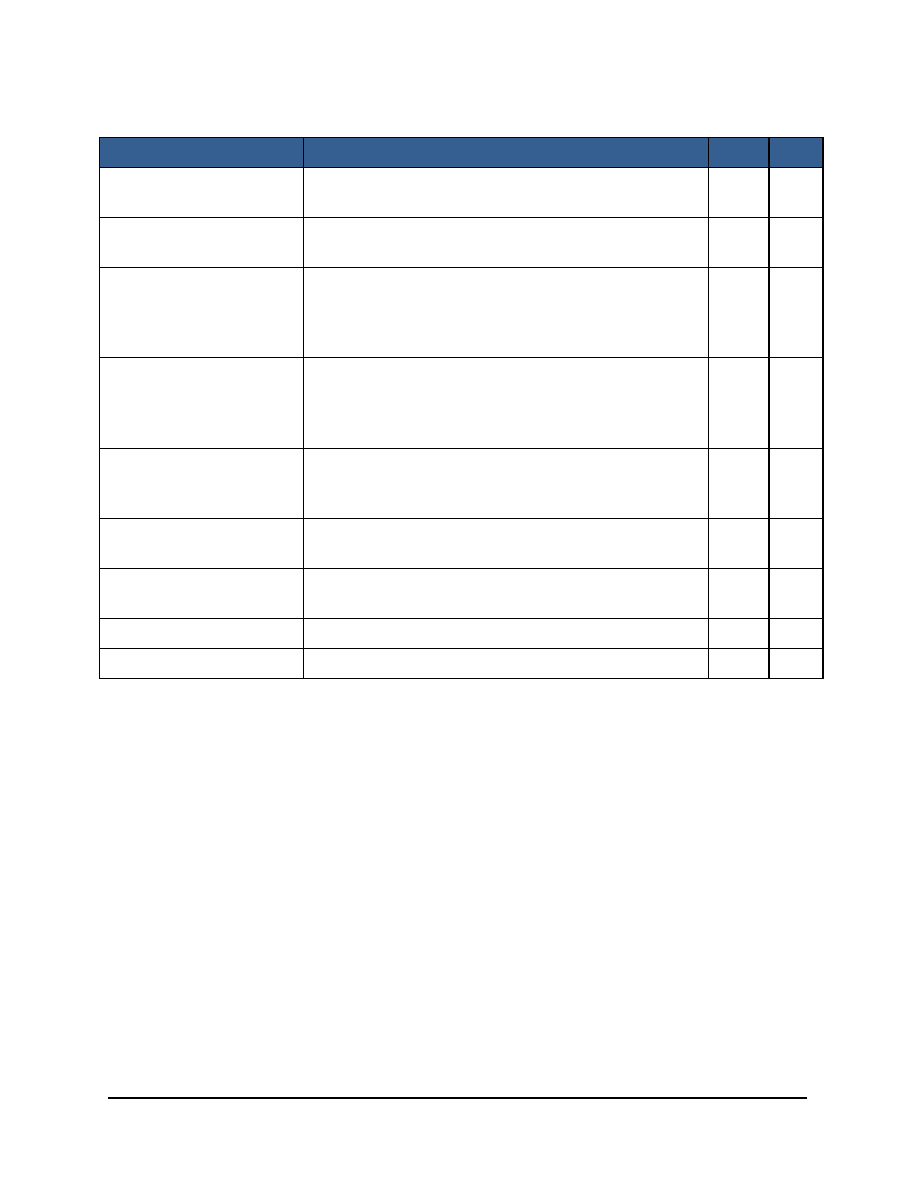
Table 8 Services
Service
Description
CO
U
Data
Storage
Encrypt/
Decrypt
Provides data encryption / decryption for calling
application.
X
DEKEK Import/Export in
plaintext
The DEKEK is exported by the module, transformed by
the calling application, and re-imported.
X
DEK
Import/Export
in
encrypted form
When the configuration is changed, the DEK is wrapped
by the DEKEK and exported. The wrapped DEK is
imported (by the calling application) on module's power-
up.
X
DEKEK Import/Export as
split-knowledge
After a new DEKEK is generated, the keys are exported in
split-knowledge form. They are stored by the calling
application. On demand, the DEKEK is imported in split-
knowledge form, (provided by the calling application).
X
SP 800-90A DRBG
Provides random numbers to the calling application, also
serves to generate keys such as DEKEK and DEK and
export them immediately.
X
Module Power-on (Run
self-tests)
The module runs all self-tests implicitly at power-up.
X
Show Status
The module automatically calls the FOEd logging service
as events, such as power-up, occur.
X
Show Version
Display the version of the module
X
Zeroize
Destroys all CSPs by powering down the physical GPC.
X
Table 14 defines the relationship between access to CSPs and the different module services. The modes
of access shown in the table are defined as:
G = Generate: The module generates the CSP.
R = Read: The module reads the CSP. The read access is typically performed before the module
uses the CSP.
E = Execute: The module executes using the CSP.
W = Write: The module writes the CSP. The write access is typically performed after a CSP is
imported into the module, when the module generates a CSP, or when the module overwrites
an existing CSP.
Z = Zeroize: The module zeroizes the CSP.

