CR-4056
Rev 5
Page 8 of 22
2.3.1 Services for Authorized Roles
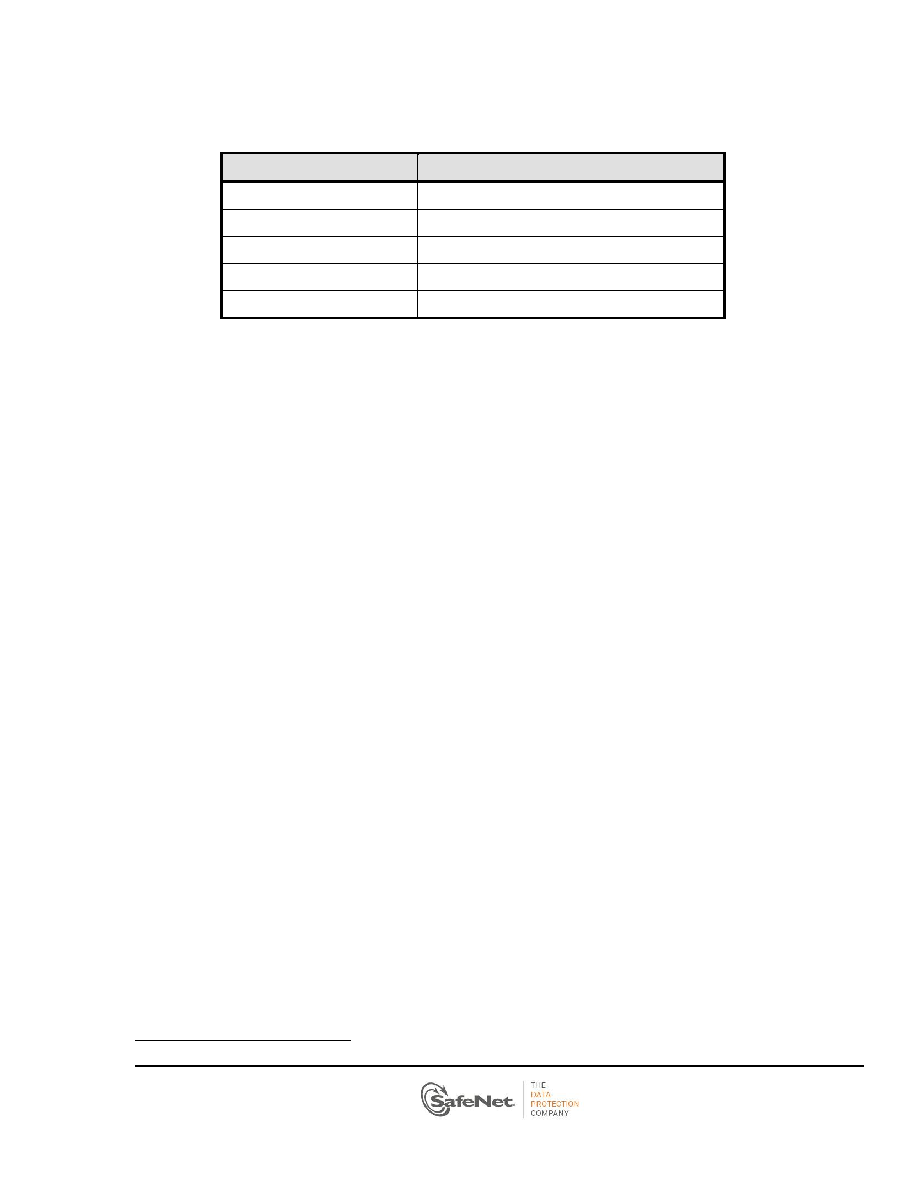
Table 2-4 lists the services related to each authorized role within the adapter:
Role
Services
Administrator SO
Initialize Administrator Token User PIN
Administrator
Manage Adapter and Administrator Token
Token SO
Manage Token
Token User
Use Token and manage token keys
Unauthenticated operator
Unauthenticated services
Table 2-4 Types of Available Services
All services listed in Sections 2.3.1 through 2.3.6 can be accessed in FIPS and non-FIPS mode. The services
Table 2-10. When the module is operating in FIPS-approved mode as described in Section 3, the Non-FIPS
Approved key derivation mechanisms in Table 2-10 are disabled and cannot be used for these services. The
non-Approved functions in Table 2-10 can only be accessed through the services when the module is in non-
FIPS Approved mode.
2.3.2 Administrator Security Officer
The primary role of the Administrator Security Officer (ASO) is to introduce the Administrator to
the system. The ASO is able to set the initial Administrator PIN value but is not able to change
the administration PIN after it is initialized. The ASO can perform the following services:
Set the initial Administrator PIN value (may not change it later).
Set the CKA_TRUSTED attribute on a Public object in the Administrator Token.
Set the CKA_EXPORT attribute on a Public object in the Administrator Token.
Manage Host Interface Master Keys
Exercise cryptographic services with Public objects
Create, destroy, import, export, generate, and derive1 Public objects
May change his/her own PIN
Read the Hardware Event Log
May modify Monotonic Counter object
Power-up self-test on demand
2.3.3 Administrator
The Administrator is responsible for the overall security management of the adapter. Token
Security Officers and Slots are controlled by the Administrator. The following services are
available to the Administrator:
Set or Change RTC value

