CR-4056
Document is Uncontrolled When Printed.
Page 16 of 22
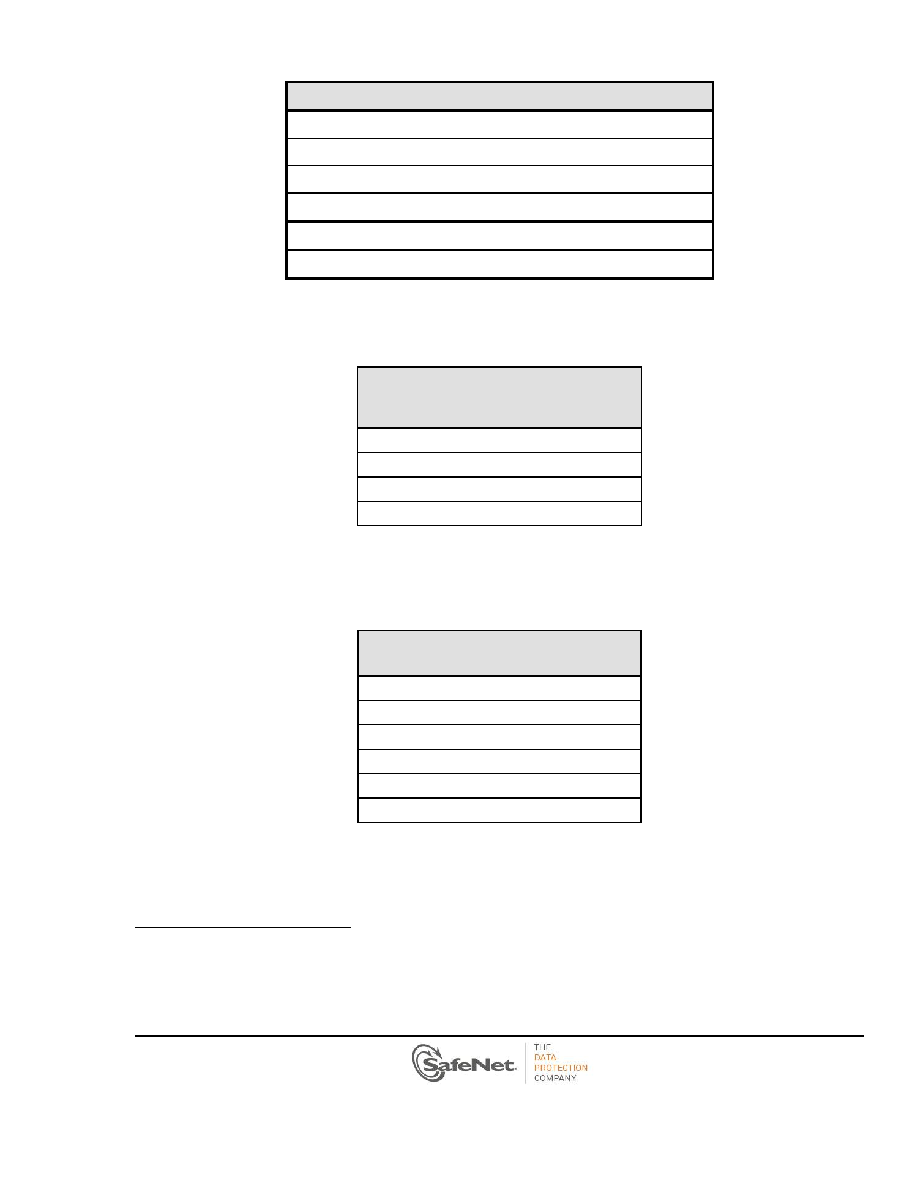
Non-Approved FIPS but Allowed Security Functions
AES5 Key Wrapping/Unwrapping
Triple-DES6 Key Wrapping/Unwrapping
Diffie-Hellman Key Agreement/Key Establishment7
RSA Key Wrapping/Unwrapping8
EC Diffie-HelmanH9 - Only NIST Recommended Curves
NDRNG
Table 2-8 Non-Approved FIPS Allowed Security Functions
Table 2-9 lists the PSI-E2 key derivation mechanisms that are non-Approved but Allowed in FIPS mode.
MECHANISMS FOR SPLIT KNOWLEDGE
ENTRY/OUTPUT OF KEY
(Allowed in FIPS Mode)
CKM_CONCATENATE_BASE_AND_KEY
CKM_XOR_BASE_AND_DATA
CKM_XOR_BASE_AND_KEY
CKM_SECRET_SHARE_WITH_ATTRIBUTES
Table 2-9 Non-Approved FIPS Allowed Key Derivation Mechanisms
Table 2-10 lists the PSI-E2 key derivation mechanisms that are non-Approved and not Allowed in FIPS mode.
These key derivation mechanisms are actively disabled by the module when operating in FIPS mode.
NON-ALLOWED DERIVATION METHODS
(Disabled in FIPS Mode)
CKM_DES3_DERIVE_CBC
CKM_DES3_DERIVE_ECB
CKM _SHAxxx_KEY_DERIVATION
CKM_SSL3_KEY_AND_MAC_DERIVE
CKM_SSL3_MASTER_KEY
CKM_EXTRACT_KEY_FROM_KEY
Table 2-10 Non-Approved Key Derivation Mechanisms
5 AES key wrapping; key establishment methodology provides 128, 192 or 256 bits of encryption strength;
6 Triple-DES key wrapping; key establishment methodology provides 112 bits of encryption strength);
7 Diffie-Hellman key agreement; key establishment methodology provides between 112 and 150 bits of encryption strength;
8 RSA key wrapping; key establishment methodology provides between 112 and 150 bits of encryption strength;
9 EC Diffie-Hellman (ECDH) (curves in accordance with SP 800-57) key agreement, key establishment in accordance with NIST SP 800-
56A. key establishment methodology provides 112 or 128 bits of encryption strength

