CR-4056
Document is Uncontrolled When Printed.
Page 14 of 22
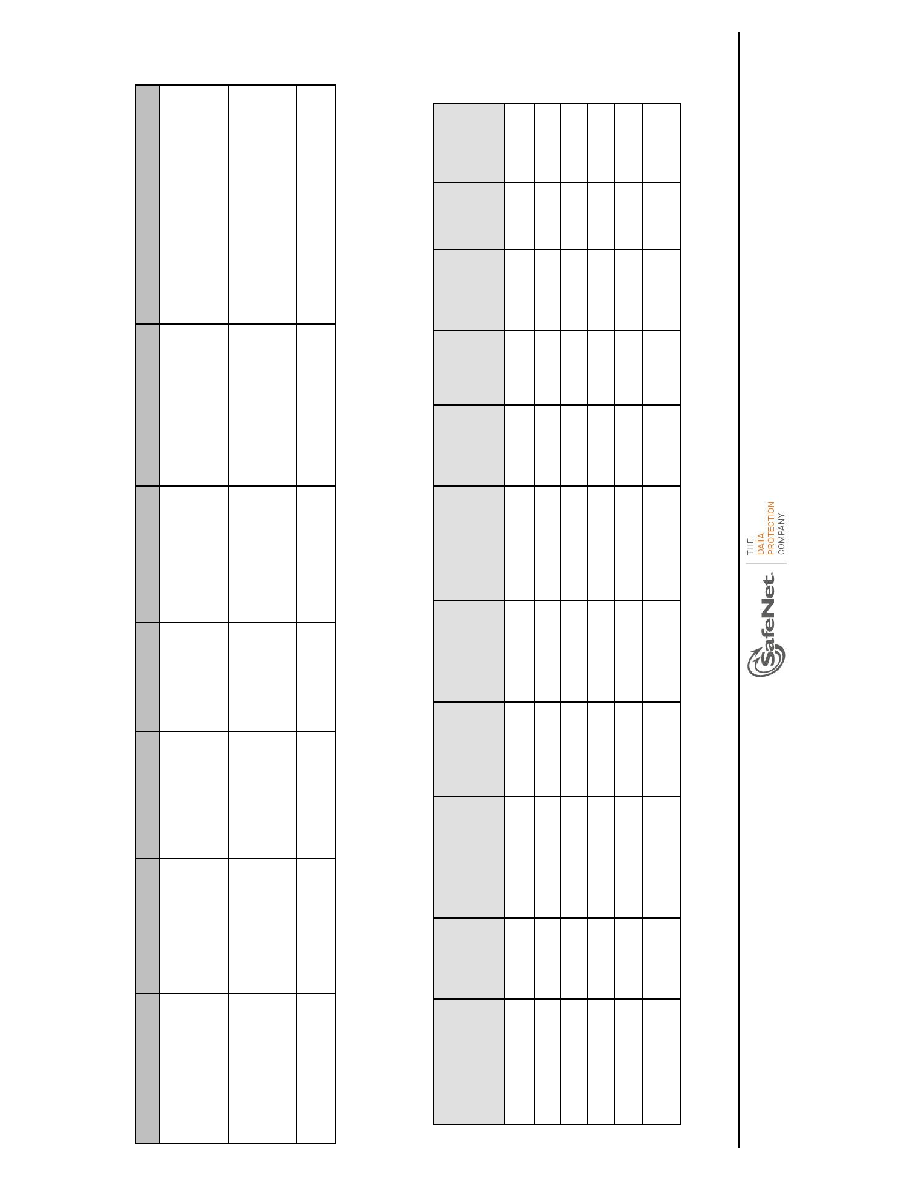
CSP
CSP Type
Generation
Input/Output
Storage
Destruction Mechanism
Use
DSA Public/Private
Keys
2048
4096 bit DSA
FIPS 186-4
Public key
exported
Working memory or
Secure Memory
encrypted with MMK
Power cycle, tamper, or
C_DestroyObject() API
User-created keys for use by user
applications for encryption, Decryption,
Key wrapping/Unwrapping and
Signature Generation/Verification
ECDSA Public/Private
Keys
224
512 bit
ECDSA
FIPS 186-4
Public key
exported
Working memory or
Secure Memory
encrypted with MMK
Power cycle, tamper, or
C_DestroyObject() API
User-created keys for use by user
applications for encryption, Decryption,
Key wrapping/Unwrapping and
Signature Generation/Verification
DRBG Seed
Seed
H/W RNG
Not input/output
Not permanently
stored
Power cycle or tamper
Used as part of the RNG process.
Table 2-5 List of Keys Stored in Module
outlines the access that "Authorized Services" (see Table 2-4) have to the keys listed in Table 2-5. Here `R' stands for "Read", `W' stands
for "Write", X stands for "Execute" and "Z" stands for "Zeroize".
FW
Upgrade
Cert
Default
Administrator
Token SO PIN
DH / ECDH
Ephemeral
Keys
Key
Agreement
Keys
Message
Authentication
Key
Operating
PINs
Token
Keys
(Public)
Token
Keys
(Private)
RNG
Seed
Module
Master
Key
Initialization
-
-
-
X
-
WX
-
-
-
W
Administrator SO
WX
WX
-
WXZ
-
WXZ
RWXZ
RWXZ
-
RWXZ
Administrator
-
-
WZ
X
WZ
WXZ
-
-
-
RWXZ
Token SO
-
-
RXZ
X
RXZ
X
-
-
-
-
Token User
-
-
RXZ
X
RXZ
X
XZ
XZ
XW
-
Unauthenticated
Operators
-
-
-
-
-
X
-
-
-
-
Table 2-6 Access to Keys for Authorized Services

