Copyright © 2014 Fiber Logic Communication, Inc.
This document may be reproduced only in its original entirety. [without revision]
11
5. Critical Security Parameters
The following are the Critical Security Parameters (CSPs) used in the module.
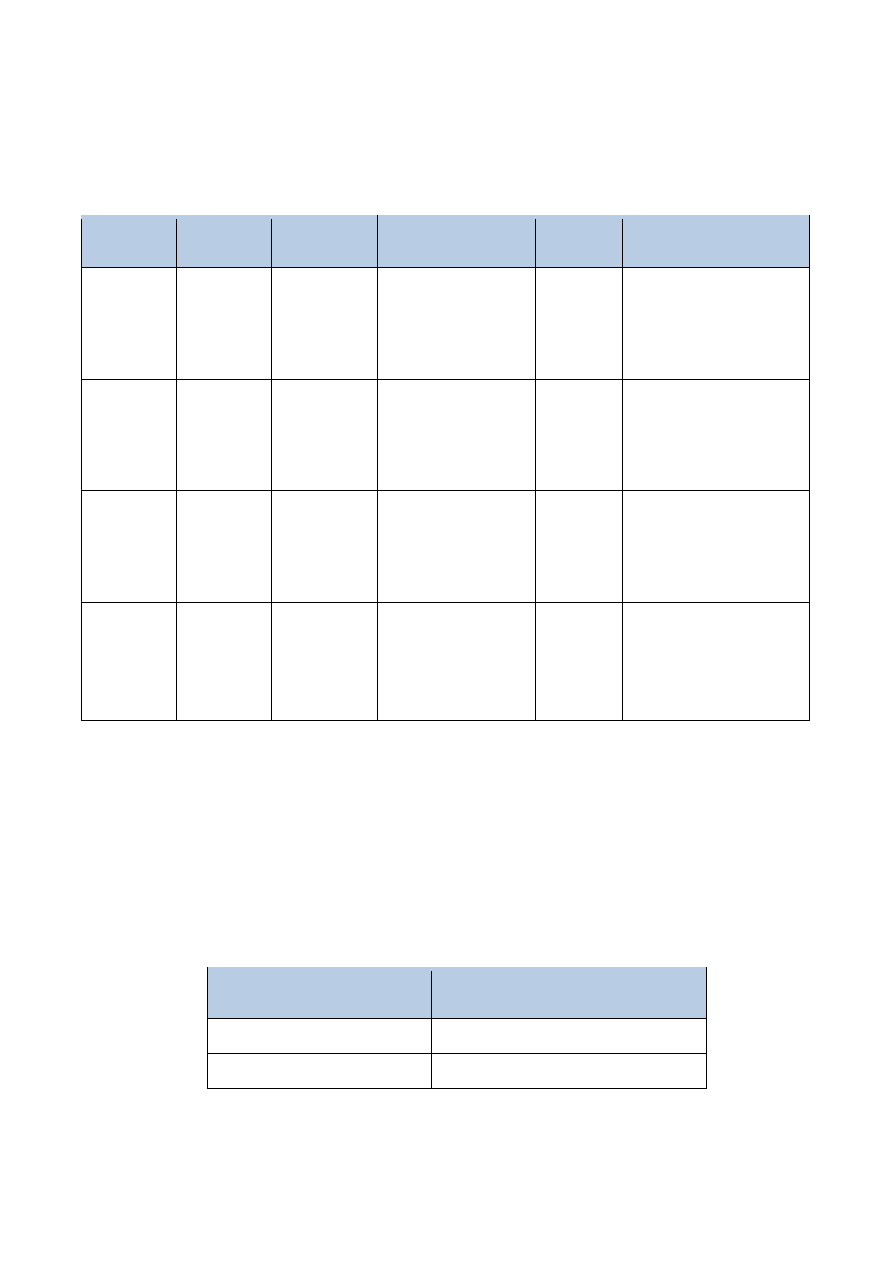
Table 5-1
Critical Security Parameters
CSPs
CSP type Generation
Use
Stored
Zeroized
Data
session
keys
128/192/2
56-bit
AES keys;
Imported
from KeyIn
port.
Secure data traffic. Battery
backed
SRAM
1.On tamper detected
2."Zeroize keys &
CSPs" service.
3. Key reset button is
triggered.
HMAC key Fixed
length,
512-bits
HMAC key
Imported
from KeyIn
port.
Used for checking
firmware integrity
and authentication
code during
firmware load test.
Battery
backed
SRAM
1.On tamper detected
2."Zeroize keys &
CSPs" service.
3. Key reset button is
triggered.
Key
wrapping
key
256-bit
AES key
Imported
from KeyIn
port.
Used to encrypt
keys imported into
the module using
external key
loader.
Battery
backed
SRAM
1.On tamper detected
2."Zeroize keys &
CSPs" service.
3. Key reset button is
triggered.
Username
/Password
Operator
username,
6~20
characters
password
Entered by
operators
Authentication for
accessing the
management
interface.
Battery
backed
SRAM
1.On tamper detected
2."Zeroize keys &
CSPs" service.
3. Key reset button is
triggered.
6. Identification and Authentication Policy
6.1 Roles
The TS-250 cryptographic module supports identity-based authentication. There are
two roles in the module (as required by FIPS 140-2 Level 3) that operator may assume:
Crypto-Officer role and User role. The module has two default operators: co and user.
Table 6-1
Default Operators
Username
Role
co
Crypto-Officer
user
User

