All Rights Reserved. Copyright © 2012, Hitachi Solutions, Ltd.
This document may be freely reproduced and distributed whole and intact including this copyright notice.
8
operating system (OS) 32-bit user mode/64-bit user mode, and Linux
3 OS 32-bit user mode as in
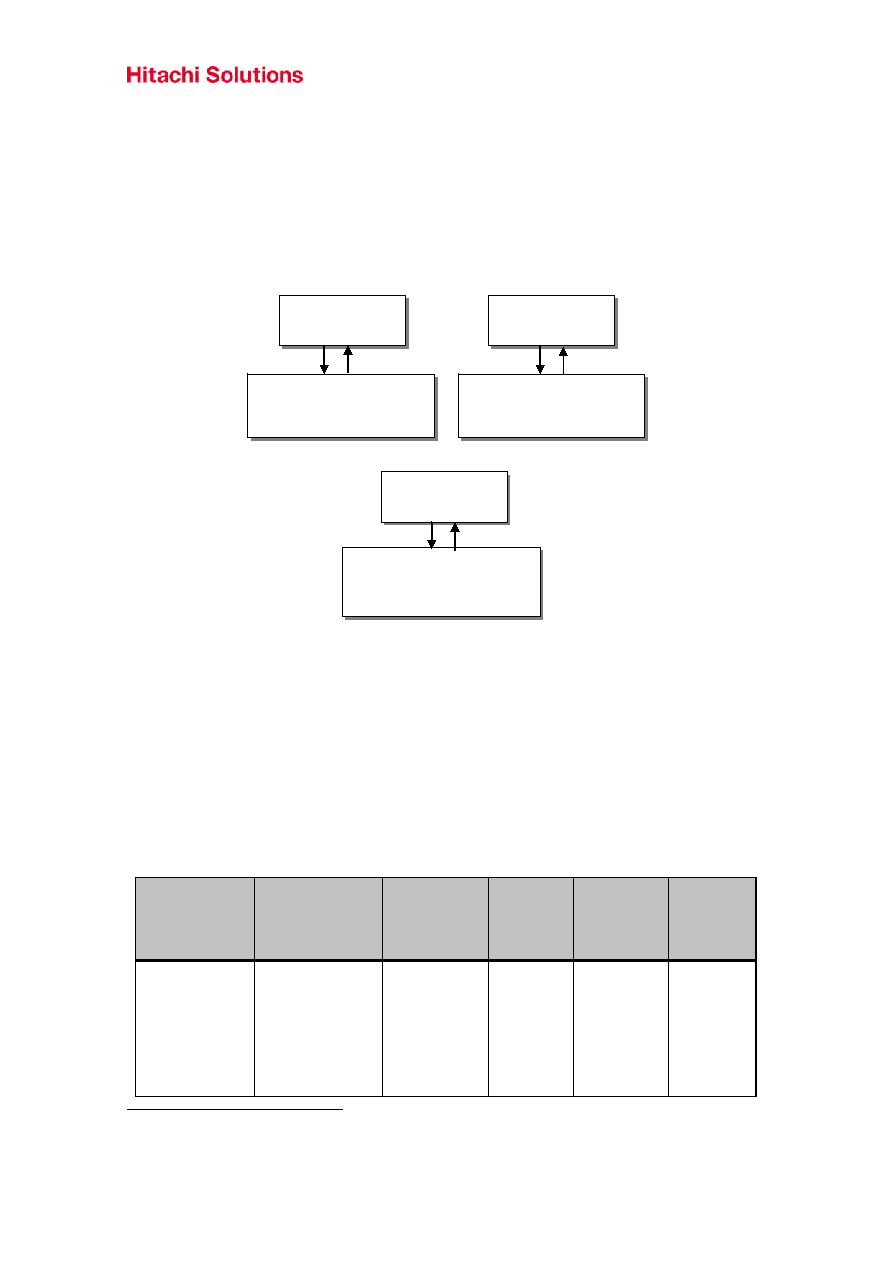
Figure 2. In Figure 2, each arrow indicates the relationship between the cryptographic library module
and calling applications.
All the security requirements in Table 1 are applied to all the cryptographic library modules above.
Figure 2: Relations between the HIBUN Cryptographic Module and OS
2.5.
Algorithms
The cryptographic library module provides symmetric key cipher, message digest, message
authentication, and pseudo-random number generation of the security functions approved by FIPS
140-2. Table 2 shows the FIPS 140-2 approved security functions provided by the cryptographic
library module.
Table 2: Approved Algorithms
Service
Algorithm
Mode
FIPS140-2
Approved
Publication
Algorithm
Certificate
Number
Symmetric
Cipher
AES
Encrypt/Decrypt
(128 bit)
ECB, CBC,
CFB 8 bit,
CFB 128 bit,
OFB
Yes
FIPS 197
1780
3
Linux is a registered trademark of Linus Torvalds.
Windows
Application (32 bit)
Windows
HIBUN Cryptographic Module
(Windows User-Mode 32 bit)
sxdcryfp.dll
Linux Application
(32 bit)
HIBUN Cryptographic Module
(Linux 32 bit)
libsudcryfp.so
Linux
Windows
Application (64 bit)
HIBUN Cryptographic Module
(Windows User-Mode 64 bit)
sxqcryfp.dll
Input
Output
Input
Output
Input
Output

